A longstanding debate on online tech forums has centered around the discussion of the hand Antivirus software companies may or may not play in the creation and distribution of computer viruses.
Forum contributors believe the Antivirus companies create these viruses to bolster the sales of their antivirus software and/or to scare/impress potential clients into buying the software.
The antivirus companies have with good reason vehemently denied these claims chalking it all up to urban myths for ignorant computer users. Human beings have shown time and again their propensity for unwarranted malicious intent towards strangers without any expected gain, monetary or otherwise with the development of viruses.
That is how the situation has been until the skyrocketing trend of Ransomware infections affecting the developed world.
Ransomware is a type of malware that restricts access to the infected computer system in some way, and demands that the user pay a ransom to the malware operators to remove the restriction.
Some forms of ransomware systematically encrypt files on the system’s hard drive, which become difficult or impossible to decrypt without paying the ransom for the encryption key, while some may simply lock the system and display messages intended to coax the user into paying.
Ransomware typically propagates as a trojan, whose payload is disguised as a seemingly legitimate file; thus, ransomware is an access-denial type of attack that prevents legitimate users from accessing files. ~ Wikipedia
Most affected are companies, hospitals, schools and individuals. The attackers are so far mostly targeting wealthy countries in Europe and the Americas where victims are expected to pay a higher ransom and do have more sensitive information stored on their computers which they stand to lose if they don’t comply.
The Cybercriminals use country-specific IP addresses and email addresses with country codes such as .uk and .au to pinpoint the location of their intended victims. Ransomware attacks are not prevalent in Africa with the exception of South Africa which is facing the brunt of the attacks.
Ransomware worldwide distribution
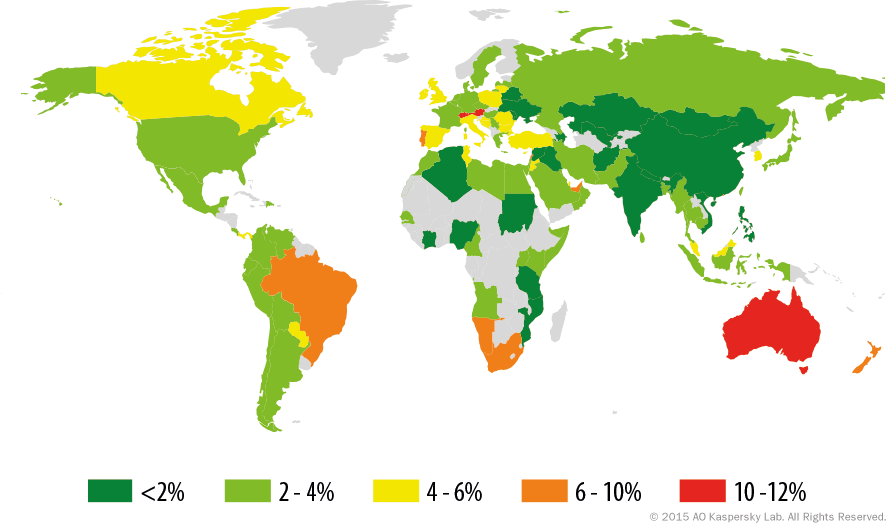
Data: Kaspersky Labs, covering Kaspersky clients worldwide
The Ransomware comes in the form of a legitimate-looking email attachment, a link or a malicious ad in your browser. When you click on it, nothing drastic might happen on the surface but behind the scenes, the Ransomware gets to work downloading itself and quickly encrypting files on your local drive and any attached drives.
Next time you need to access your files you will be informed that to access said files, you need to pay a ransom of a certain amount for the Cybercriminals to decrypt your computer. Payment is usually in Bitcoin, preferred by the criminals because tracing money in Bitcoin is nigh impossible at the moment.
Antivirus software don’t appear to be much help at detecting and cleaning Ransomware. Kaspersky Labs, the makers of Kaspersky Antivirus have nonetheless been successful in decrypting a number of ransomware raising hopes at point in the near future, this scourge will be manageable or better still eradicated completely.
- Ransomware attacks PCs, Macs, Smartphones and Servers, e.t.c.
- Targeted are organisations, companies, schools, hospitals, government parastatals, and individuals.
- Cybercriminals mostly target wealthy countries
- The Ransomware code is hidden in legitimate-looking email attachments, links and malicious ads in your browser
- Antivirus software might not detect most ransomware
- Local hard drive files are encrytped with crypto-ransomware that can only be unlocked after paying a ransom
- Bitcoin is most preferred ransom payment currency
Related: WannaCry, Ransomware and Bitcoin: What you need to know to protect yourself from Cybercrime
FBI Tips for Dealing with the Ransomware Threat
While the below tips are primarily aimed at organizations and their employees, some are also applicable to individual users.
Prevention Efforts
– Make sure employees are aware of ransomware and of their critical roles in protecting the organization’s data.
– Patch operating system, software, and firmware on digital devices (which may be made easier through a centralized patch management system).
– Ensure antivirus and anti-malware solutions are set to automatically update and conduct regular scans.
– Manage the use of privileged accounts—no users should be assigned administrative access unless absolutely needed, and only use administrator accounts when necessary.
– Configure access controls, including file, directory, and network share permissions appropriately. If users only need read specific information, they don’t need write-access to those files or directories.
– Disable macro scripts from office files transmitted over e-mail.
– Implement software restriction policies or other controls to prevent programs from executing from common ransomware locations (e.g., temporary folders supporting popular Internet browsers, compression/decompression programs).
Business Continuity Efforts
– Back up data regularly and verify the integrity of those backups regularly.
– Secure your backups. Make sure they aren’t connected to the computers and networks they are backing up.
Find the complete list of precautions on the FBI CyberDivision webpage. Uganda too has a Cyber division, Computer Emergency Response Team –CERT.UG– which ‘strives to effectively analyse and respond to the major computer security incidents in Uganda with provision of services and support arising from best practices to inhibit and reduce damages.’
Among the security tips advised is never to open email attachments from suspicious or unknown sources. When we clicked on some of the links on the CERT UG website, we were directed to an online newsletter leading us to believe CERT is either automated or understaffed.
Discover more from Dignited
Subscribe to get the latest posts sent to your email.