Have you ever wondered if a VPN really does much for your privacy and security when you are online? VPNs have always been our go-to means to mask our online identity and help us have access to geo-restricted content.
But history has proven to us that VPNs are not always a silver bullet for privacy and digital security and because running a VPN requires money, VPN providers will also ask free service customers to consent to other ways of making money, which may include tracking and selling their private data.
This entails people looking for other avenues to stay safe online. In this guide, we will look through over 10 ways to practice digital hygiene and keep safe without having to use a VPN.
But First, Let’s Look at How Your Devices Connect to the Internet
The thing is most VPN providers market their premium service as an arsenal of ammunition that helps with online security and privacy and always comes out as the only solution you will need. Looking at the fundamentals of how your gadgets connect to the Internet might be helpful in demystifying such claims and help you make an informed decision before spending on a premium VPN.
You see, when your computer or phone connects to the internet, it sends packets tagged with a source and destination IP address. It traverses a series of Internet Service Providers(ISPs) to reach its final destination. Anything logging traffic in between(WireSharks) can see your source IP address, which can be geolocated to within a few blocks of your home. Your IP is shared by a million other people, so it’s only an approximate location, not where you sleep at night.
With a VPN, the original packets get encrypted and wrapped in another IP header with the VPN server as the destination address. The VPN server will unwrap the packet and forward it through its own ISP, using its own IP address as the source.
Devices sitting before the VPN server can see your IP but not the destination. Meanwhile, devices sitting after the VPN server can see the destination but not the source. The zones within the network path are now partitioned.
Focusing on just the IP header is just like focusing on the tip of an iceberg. When you look at the network packet, metadata is spread across all the OSI model layers. Depending on the vantage point of an observer in your network path, there is different visibility into your packets. And that, in a nutshell, is the primary reason why you can’t trust a VPN to protect your online identity.
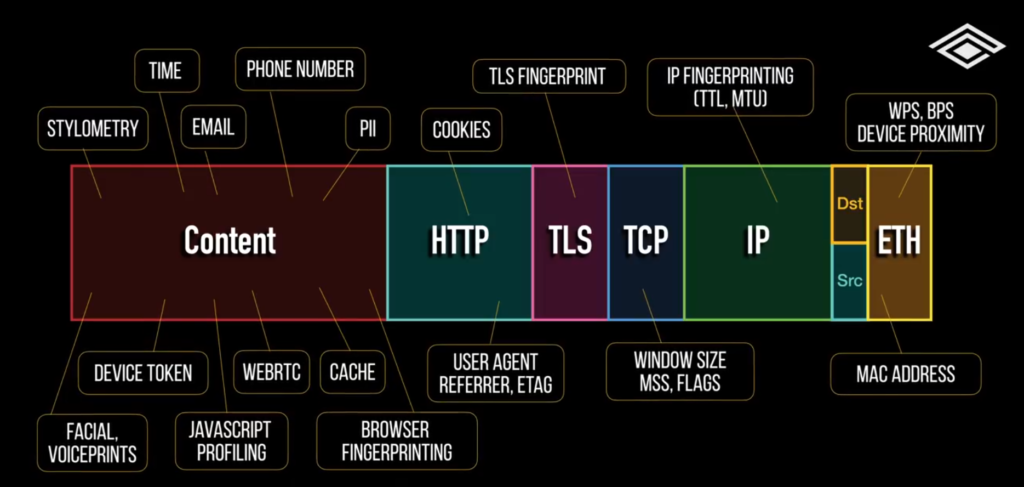
Every piece of software you install, be it software or an app or plugin, can potentially be malicious and surveil your data and activity before it leaves your device.
On the local network, there is layer 2 addressing information that lets tech companies identify your location without an IP address through WiFi or Bluetooth positioning. Looking at proximity and signal strength to nearby devices with known geolocations like your friend’s phone, smartwatch, or wireless access point can help pinpoint your device too.
Your local ISP probably knows you are using a VPN based on the IP header alone. Just like Tor exit nodes, there are a fixed number of VPN addresses out there to track on a watchlist. The VPN company and their ISP are privileged to see the whole packet’s metadata and can fingerprint your device type with the IP, TCP, and TLS headers. The VPN can claim not to log this stuff, but you can bet the cloud providers and ISPs servicing it are. The server you are going to can also tell you are on a VPN since the MTU size, or max transmissible unit on the packet is going to be smaller than usual since you are piling one packet inside of another.
Watchlists and this kind of fingerprinting can help sites like banks flag any VPN connections and deny you service.
Use Cases of a VPN
So you know, you might be wondering what the use cases of a VPN are, or should I even try to mask my IP address? First, you have to gauge your level of threat. Is it cybercrime, big tech, or your government? Understanding your level of threat helps tailor your level of paranoia accordingly, so it’s not over or underweight.
There are cases where you masked your IP address and this includes but is not limited to;
- Cirmuventiing IP blocks to watch Netflix and geo-restricted content.
- Getting around national firewalls, when certain websites or apps are blocked in your country.
- Bypassing downloads limits
- Performing offensive security assessments
- Conducting OSINT and research
For most people, practicing digital hygiene and cleaning up your online identity isn’t that complicated. Here are tips you can use to keep safe on the internet without having to use a VPN:
- Use a unique password for every site.
- Use a unique email for every site.
- Use hardware security tokens for 2-factor authentication.
- Use random answers for recovery questions.
- Go through all your privacy settings on all your accounts. Sanitize your social media.
- Use virtual machines and multiple phones for different kinds of activity.
- Don’t click links or scan QR codes without first analyzing them.
- Set up a commercial address so you don’t receive it at home.
- Keep apps to a minimum and avoid pirated software.
- Use a host-based firewall to alert on outbound connections that you need to manually verify for every app.
- If you are traveling and tempted by public WiFI, just bring your own internet through portable hotspots or tether off your phone.
None of these options involve using a VPN, yet they do far more for your security and privacy overall. Share with us in the comment section your thoughts and opinions on how you keep safe on the internet. Is there anything special you do that we missed?
Discover more from Dignited
Subscribe to get the latest posts sent to your email.