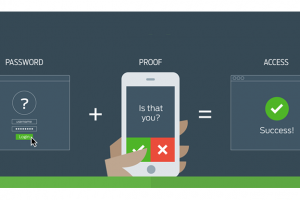
Multi-factor authentication (MFA) is a method of confirming a user’s claimed identity in which a user is granted access only after successfully presenting 2 or more pieces of evidence (or factors) to an authentication mechanism. This effectively offers an extra layer of security. Using MFA to secure your account mean you require not only a password and username but also something that you, and only you have.
Authentification Factors
See, there are a few ways that you can identify yourself to a computer system. Broadly, these are classified into three major categories;
- Knowledge Factor
- Possession Factor
- Inherence/Biometric identifiers
Knowledge factor- This is the most commonly used method of authentication. It is something that only the user knows. These include Passwords, PIN codes, personal questions like where you were born, swipe patterns…you get the idea.
Possession factor- These are physical items like security swipe cards, something only the user has, eg your ATM card at the ATM machine.
Inherence/Biometric identifiers – this something only the user is. These include our Fingerprints, Iris, facial recognition, voice prints, DNA, just to mention a few.
Of all these three methods of authentication, Biometric is the least preferred. This is because it can easily be replicated once it has been compromised. And you can’t exactly change your fingerprint like you can change your passwords now, can you?
Two-Factor Authentication
So now what is Two-Factor Authentication? As mentioned above, It is a method of confirming a user’s identity by utilizing a combination of two different factors: 1) something they know, 2) something they have, or 3) something they are. For example, you can combine a knowledge factor like say your pin or password with a possession factor like a key card or more commonly, your phone. Two-factor authentication is the most popular multifactor authentication used online. WordPress, Google, Facebook, twitter, steam, apple among many more
A good example that is often used is you at the ATM. It takes a possession factor, your ATM Card, and a knowledge factor, your PIN, in the right combination (right Card and right code) to access your money.
How does Two-Factor Authentication work?
As of 2018, the most commonly used 2FA method used is SMS. Dropbox, WordPress, Facebook, Twitter and Google all use SMS as the basis of their 2FA. To use it, a user opts into the verification method and links their mobile phone number to their online account.
In the event that the user wants to log in, he will first sign in the normal way, using their username and password. After that, an SMS with a unique code is sent to their phone by SMS. The user then keys in the received code and is allowed access to their account.
In 2016 and 2017 respectively, both Google and Apple started offering user two-step authentication with push notification as an alternative method
Why is 2FA not mainstream yet
To some extent, it really has gone mainstream. A lot of security-conscious people already use some form of Multi-Factor-Authentication to secure their accounts. However, there are some platforms that don’ quite support any form of 2FA.
This form of authentication doesn’t quite work for people who share accounts. Only the party with the one physical identifier can have access to the account at any one given time.
If you really do care about your data privacy and your security online, setting 2FA and using it is an effort that is absolutely worth it. In this day and age where even big companies like Yahoo! can get compromised, no one is safe. Setting up and using 2fa guarantees you some level of security. Even if your password or PIN is compromised, unless the attacker has your phone, they won’t have access to your data.
Featured image: www.netsafe.org.nz
Discover more from Dignited
Subscribe to get the latest posts sent to your email.