Cybercriminals have been always making malicious software (Malware) to do stuff like steal your precious data. The security industry has also been thinking up creative names for these schemes. Trojans, worms, ransomware, etc. One of the most sinister forms of malware prevalent today is the dreaded “Rootkits”. Rootkits can be very unpleasant on your PC.
What exactly are they and why can they be more problematic than other types of computer infections? Well, like with a lot of the other threats to your system, the name rootkit reveals a lot. It’s derived from the concept of root access in the operating system. Root access allows a user broad permissions to change files and settings.
Related Article: Top 5 file extensions you should be cautious about
How Rootkit Works
The means by which different rootkits access off-limits parts of the computer differ. All rootkits serve the same general function — to conceal either their own presence or the presence of another piece of malware. Thus it can carry out its nefarious deeds on your system without your knowledge. It’s because of this concealing behavior that rootkits are often very difficult to remove.
As many users in the mid-2000s found out when Sony shipped tons of music CDs with rootkits designed for copy protection. These rootkits hid the Digital Rights Management (DRM) software which limited what users could do with their optical drives. Also, it caused serious system slowdowns and introduced security flaws that other malware creators took advantage of.

Finally, when Sony released a removal tool after news of the rootkit went viral. It caused even more issues. How do rootkits hide anyway? Some rootkits self inject themselves into your programs. Somewhat, like traditional computer viruses.
Related Article: What is a Firewall on a computer?
Kernel Rootkits
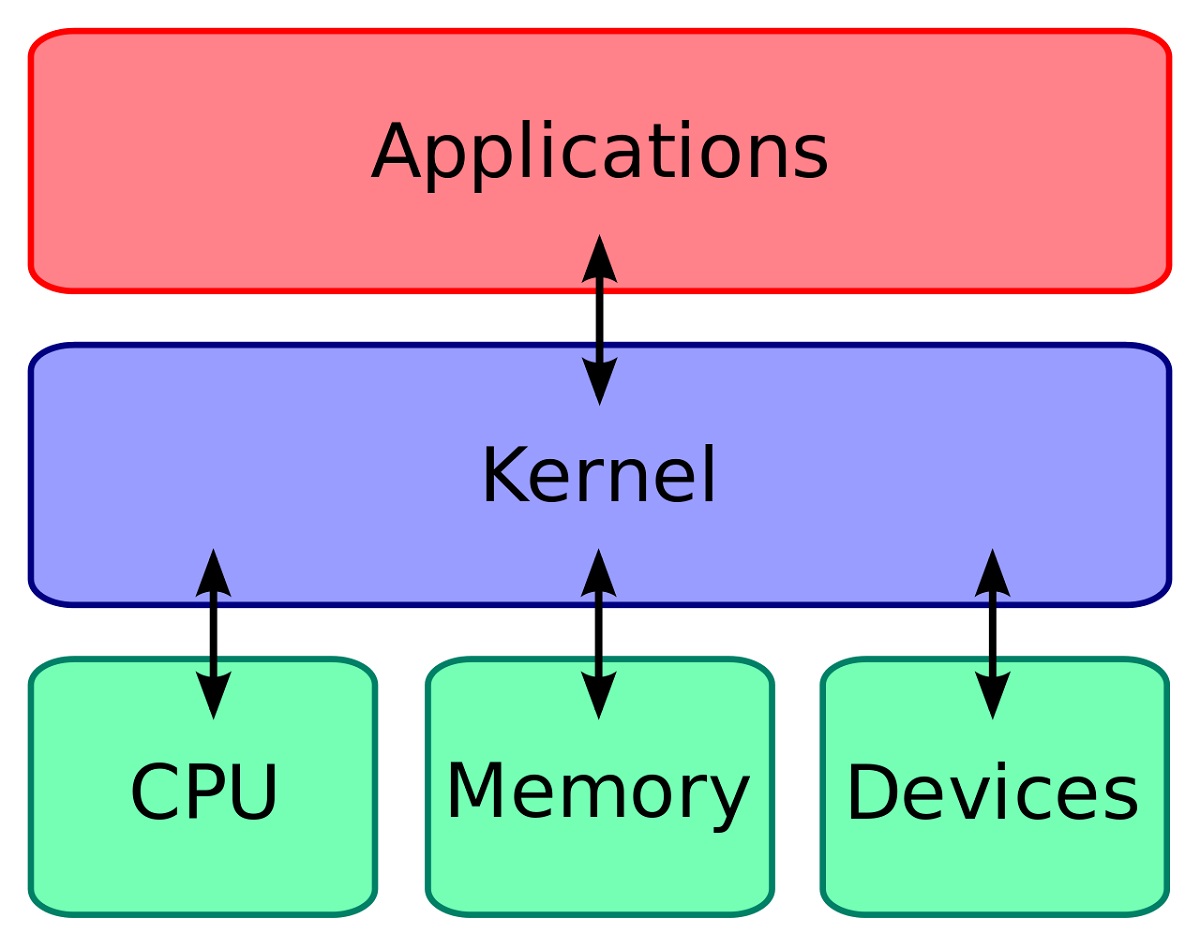
The more dangerous forms run as part of your operating system (OS) kernel. The kernel is the core part of your OS that allows your programs to communicate with your hardware. Since drivers usually run in kernel mode, many rootkits disguise themselves as drivers. This is why you should only download drivers from trusted sources — from the manufacturer’s website, for example.
What makes kernel-mode rootkits so insidious is that they essentially appear to be a part of the OS itself. Meaning you can’t really trust your antivirus program to detect it. As if that weren’t bad enough, other kinds of rootkits go as far as contaminating the hard drive boot sector. This is often done to break encryption or to get into your system’s firmware, such as your motherboard or GPU BIOS.
Related Article: All you need to know about malware: Trojan, viruses, rootkit, ransomware, spyware
Related Article: Do you still need Antivirus software?
If that happens, not even completely reformatting your PC will help. So if you don’t even know you have a rootkit, how can you get rid of them? Admittedly that is a challenge, larger organizations have tried strategies like logging suspicious access requests through a firewall. Or even dumping everything in the system’s memory to look for malicious code. But these aren’t the kinds of things a home user can easily do.
Modern motherboards with UEFI have features to block rootkit. An example is ‘secure boot,’ but this solution limits a user from doing legitimate things like installing multiple operating systems.
That said, while some simpler rootkits can be detected and removed by your favorite anti-malware program, the best counter-strategy is to just be careful about what you download.
Discover more from Dignited
Subscribe to get the latest posts sent to your email.