Security




A Beginner’s Guide to using Password Managers
With the increasing rate of online hacking, you need strong unique passwords for each of your online accounts. If you are still using your date of birth, you are in real trouble because these passwords are easy to manipulate. This is where the use of... Read More

Advertisement




Does using a VPN consume more data?
Yes, it does but not by a big margin. With online security becoming a day-to-day need, for whichever reasons one may have, people would natuarally want to stay safe while using the Internet - and that's when the VPN comes in as a solution. But... Read More

WPA3: A look at the next generation of Wi-Fi security
With a count of nearly 9 billion Wi-Fi devices in active use around the world, more than the number of human beings in existence, the coming of next-generation wireless security protocol is a must-watch. Ever since WPA2 came to be in 2004, Wi-Fi security has been... Read More

Advertisement


Hacking Vs Cracking: What is the difference?
Hackers build, while crackers break. That would be the basic difference between hacking and cracking in relation to computer security. But the further question would be: What is built and what is broken into? There are many factors, and different players involved. Some act with... Read More



Advertisement

Your smartphone and DDoS attacks: an unwitting love story
Imagine someone were to tell you your Android smartphone could very likely be under the control of a cyber attacker who lives across the world from you. First would come the disbelief. No, you’d think, I’d know it if someone had some sort of control... Read More

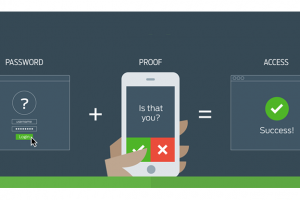
What is Two-Factor Authentication and why should you use it
Multi-factor authentication (MFA) is a method of confirming a user's claimed identity in which a user is granted access only after successfully presenting 2 or more pieces of evidence (or factors) to an authentication mechanism. This effectively offers an extra layer of security. Using MFA... Read More

Advertisement
Advertisement